Learning Logs
Sharing our logging knowledge. A place we log our insights, experiences, and findings as it pertains to the world of logs.
Sharing our logging knowledge. A place we log our insights, experiences, and findings as it pertains to the world of logs.

Logger is a command-line tool for Linux and BSD systems that allows you to easily test and send logs to syslog.
This article explains how log management fits into the security paradigm.
Article explains how log management and SIEM technology can strengthen security governance programs.
Article explains how you can use logs to deploy proactive, defensive, controls based on network activity.
Article explains what log management is and why it matters.
This article leverages logs to see the quality of leads generated by the Capterra lead generation platform.
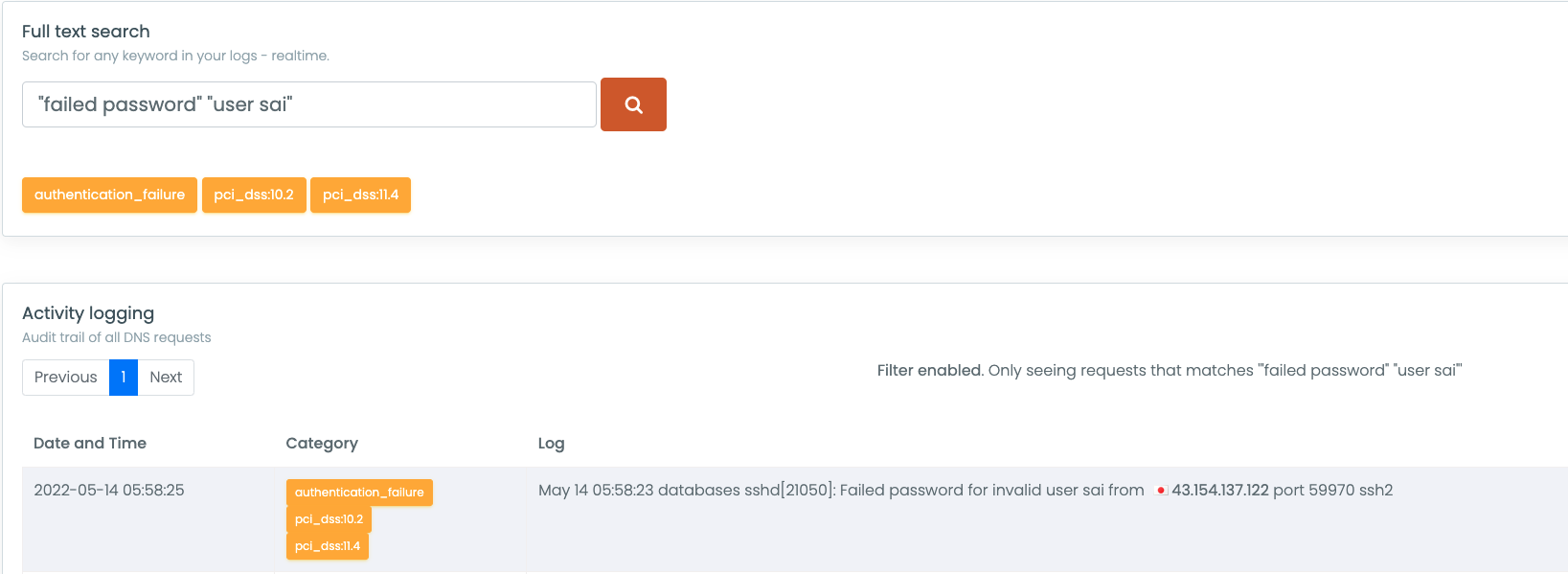
In this article we explore the best practices and the type of events that you should always store in your central logging server.
This article highlights the importance of logging, and shows how DevSecOp teams can use logs to understand what bad actors are looking for across their web assets.
Ubuntu is a popular linux distribution and this article explains how logs are generated, where they are stored, and what they capture.
The mysterious Mozlila User agent bot - attempting to compromise sites.
This article explains why it is important to include remote logging as a piece of your log management strategy.
How to troubleshoot remote syslog with tcpdump. rsyslog, syslog-ng, linux, ubuntu, red hat, centos
This article explains the differences between the different syslog daemons: syslogd, rsyslog and syslog-ng, found in Linux and BSD distributions.
Trunc provides a list of SQLi attacks in the wild. Honeypots records over 900 SQL injection attempts.
Critical logs to watch: Alerting on read-only filesystem errors
Recovering files deleted by mistake on Linux/Ubuntu using PhotoRec
Some logs require immediate response to prevent a breach or to recover a broken system. Today's critical logs are the PHP fatal errors.
The OSSEC HIDS platform is a popular log collection and analysis platform, this article shows how you can implement a web interface for the OSSEC platform.
OSSEC Log Analysis - How to get your OSSEC logs into a centralized dashboard in the cloud.
Microsoft Office365 (Azure-based) offers a very powerful audit trail of Exchange email logs. In this guide, we will explain how they look like and what to take from them.
Log management is difficult because of the shear scope of devices that need to be monitored.
Investigating and recovering a compromised Linode server running WordPress and latest Ubuntu.
HTTP User agents are a big part of how browsers and web servers communicate. In this article, we cover what they are and the most common user agents.
NGINX is the most popular web server in the planet and in this post, we will analyse their error logging in detail.
Understanding the logs from Dropbear, a SSH server meant for low memory systems. Useful to understand the logs from your routers, including OpenWrt, Ubiquiti, Unifi, etc.
Cisco Compromise - Insights from Cisco and the trails the attackers can leave in your logs.
In this article we breakdown Brute force attacks against Windows Remote Desktop (RDP) that have been happening against our server on Azure.
AWS CLI web scans looking for the AWS credentials and config files.
Analysis of a HTTP Flood - DDoS - that happened against a site that we were monitoring.
In this article we explain the two log types: access and error, and how to work with them.
This article shares the logs generated by the OWASP ZAP application security testing tool (vulnerability scanner).
NGINX is a powerful web server and logging is a critical piece to managing a web server. In this article we explain the two log types: access and error, and how to work with them.