How to use the Trunc Search
One of the key features of Trunc is the ability to parse your data from one true source, taking into account all log sources. To do this, Trunc offers a powerful parsing engine that makes searching simple.
This article will show you how to work with the Trunc search in the platform.
Configure Trunc Notifications
The Trunc parsing engine uses a very simple language, and offers a few different ways to truly extract the information you need.
By default, you can always use basic operators like AND or OR in your searches. It also offers four keywords that can help narrow the search:
| Keyword | Description |
|---|---|
| category: | These are the categories as defined in the Trunc platform (e.g., pci_dss:11.4, ids_event). |
| srcip: | This is the source IP. |
| country: | These are country abbreviations. Example: BR -> Brazil, US - United States |
| location: | This is the hostname for the source of the logs. |
| Date: | The format is YYYY-MM-DD |
| Time: | The format is HH:MM |
Example 1: Searching with Categories
We have spent a lot of time creating categories for differnt log types. This was desinged to simplify your life, and to assist with parsin.
Let's assume we're interested in all the router_logs. In this instance, I have my Ubiquiti Logs being pushed to trunc.
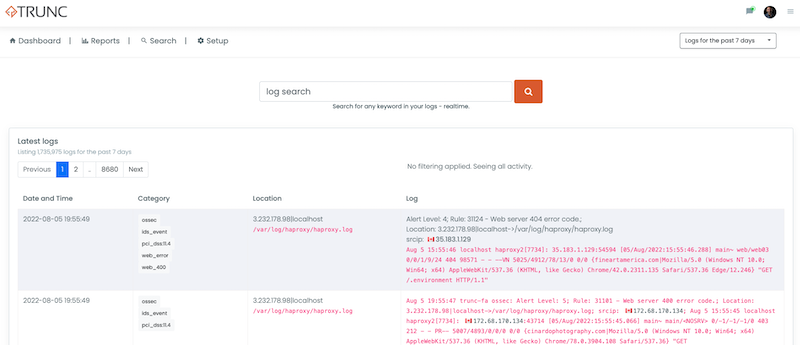
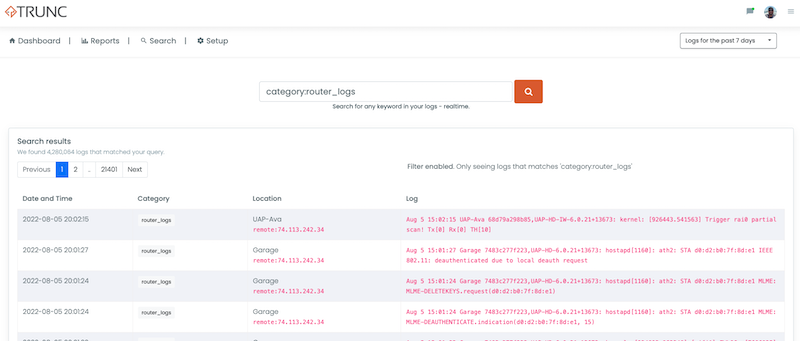
Navigating to the search panel I can do a simple search using the router_logs category like this:
category:router_logs
This will create a view like this:
Example 2: Stringing Categories Together
Altnernatively, you might be interested in analayzing data from one location, and you might be interested in one specific category.
A great example is looking at only the authentication_failure for one location (where location is the hostname).
So in this example, I want to focus on all the authentication failures on my webhonest2.noc.org location.
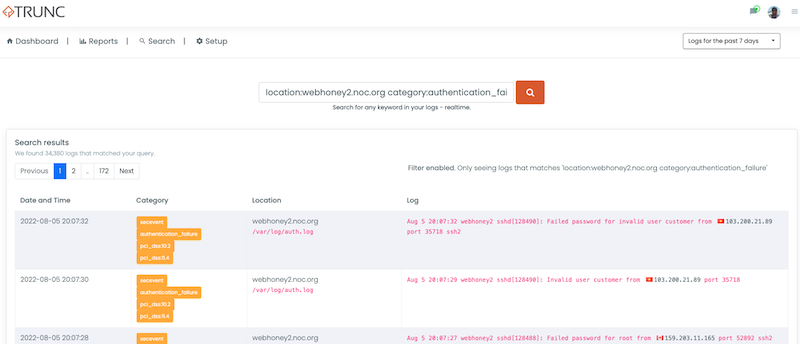
The query would look like this:
location:webhoney2.noc.org category:authentication_failure
And generate an output like this:
Example 3: Searching for Keywords / Strings
Another option might be to look for keywords, strings, of content in your logs in a specific location.
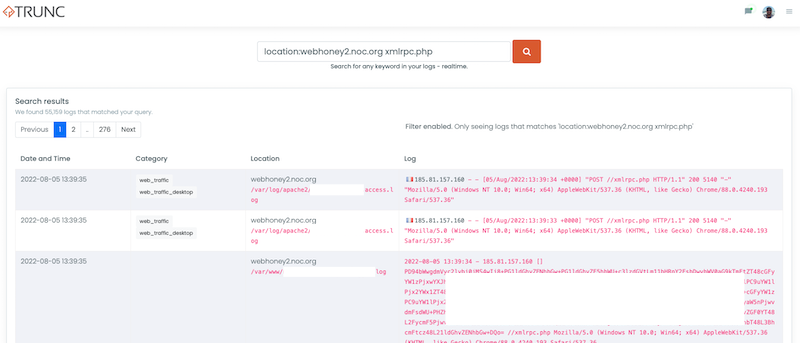
Building on Example 2, let's look for all the logs that show a hit to the xmlrpc.php file in the same location (i.e., webhoney2.noc.org)
We can run a query like this:
location:webhoney2.noc.org xmlrpc.php
And would generate an output like this:
Example 4: Searching for Two Different Things
There might also be instances where you want to search for two different things. It could be required to have both, or you might be ok with one or the other.
This is where the AND and OR operators come into play.
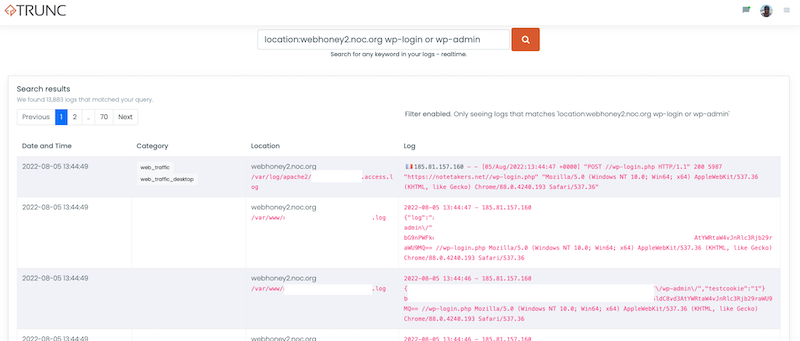
Using the same example above, let's say we're curious about all the requests hitting wp-login.php OR wp-admin on the webhoney2.noc.org host.
We would craft a query like this:
location:webhoney2.noc.org wp-login or wp-admin
And would generate an output like this:
Example 5: Searching A Specific Date
There might instances where you are only intrested in logs for a specific date..
This is where the DATE keyword helps.
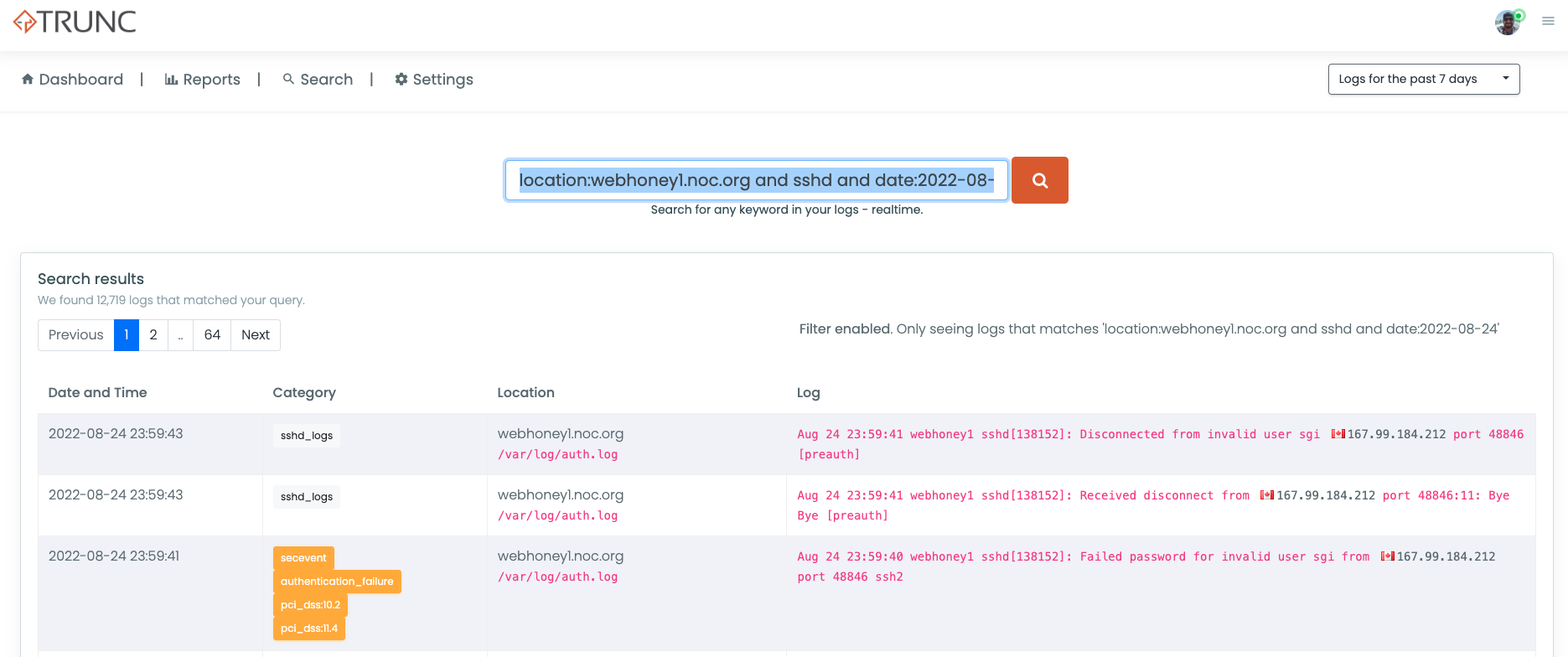
Let's say we're curious about all the requests hitting webhoney1.noc.org SSH on August 25th, 2022.
We would craft a query like this:
location:webhoney1.noc.org and sshd and date:2022-08-24
And would generate an output like this:
Posted in trunc product_configuration by trunc_team