A Guide to: Office 365 Microsoft Exchange Logs
 Oct 13, 2022
Oct 13, 2022
Microsoft Office 365 offers a complete audit trail as part of the Office 365 Management APIs. They are integrated into Azure, allowing an admin to query and fetch events from Exchange, Sharepoint, OneDrive, Microsoft Teams, Yammer,
Active Directory and Azure proper. The events are extremely detailed (generating a lot of noise because of that), it logs every event from
within Azure and Office 365.
These logs are invaluable for most organizations and exporting them to your SIEM, or log management platform, requires multiple steps (more than what it should to be honest), so we wrote
a dedicated article for it here.
Azure Management API
The Office 365 Management Activity API (or Azure API) allows you to extract 5 types of events from the activity logs:
| Event | Description |
|---|---|
| Audit.AzureActiveDirectory | Logs related to active directory. Logins, logouts, failed logins, new users, etc. |
| Audit.SharePoint | Logs related to SharePoint. Files accessed, created, uploaded, etc. |
| Audit.Exchange | Email activity. Email created, deleted, calendar action created, etc. |
| DLP.All | DLP activity. |
| Audit.General | Azure specific audit logs. |
Your logging requirements will dictate what you need to collect. This article will focus on the Audit.Exchange (Microsoft Exchange) logs.
If you are using their API directy, the Audit.Exchange logs are exported per Tenant (via the tenant_id) from this API URL:
POST https://manage.office.com/api/v1.0/{tenant_id}/activity/feed/subscriptions/content?contentType=Audit.Exchange
Note that before they are available, you need to start the subscription (start?contentType=Audit.Exchange).
Trunc will automatically handle this configuration for you.
Exchange Logs
Every event log from Azure, including the Exchange ones, are provided in JSON format. By default, it includes the following
parameters, which are part of the common audit record schema:
| Parameter | Description |
|---|---|
| ID | Unique identifier of an audit record. |
| RecordType | The type of operation indicated by the record. |
| CreationTime | The date and time in Coordinated Universal Time (UTC) when the user performed the activity. |
| Operation | The operation performed. |
| OrganizationId | The GUID for your organization's Office 365 tenant. |
| UserType | The type of user (Regular, Reserved, Admin, DcAdmin, System, Application, ServicePrincipal, CustomPolicy, SystemPolicy). |
| Workload | The Office 365 service where the activity occurred (Sharepoint, Exchange, etc). |
| ResultStatus | The result status. |
| ObjectId | The object ID (or path) involved in the operation. |
| UserId | The UPN (User Principal Name) that performed the action. |
| ClientIP | The IP address of the user. |
When analyzing logs it is critical you identify the who, from and what of any given log event. For Microsoft Exchange logs, the RecordTypes
are going to be 1,2 and 3 (for ExchangeAdmin events, ExchangeItem and ExchangeItemGroup).
This is how a raw event looks like:
[CreationTime] => 2022-09-01T19:57:49
[Id] => [event id]
[Operation] => Set-MailboxPlan
[OrganizationId] => [org id]
[RecordType] => 1
[ResultStatus] => True
[UserKey] => NT AUTHORITY\SYSTEM (Microsoft.Exchange.Servicehost)
[UserType] => 3
[Version] => 1
[Workload] => Exchange
[ObjectId] => XA001.PROD.OUTLOOK.COM/Microsoft Exchange Hosted Organizations..
[UserId] => NT AUTHORITY\SYSTEM (Microsoft.Exchange.Servicehost)
[AppId] =>
[ClientAppId] =>
[ExternalAccess] => 1
[OrganizationName] => myorg.onmicrosoft.com
[OriginatingServer] => XA00..
Trunc works to decode the JSON output provides a readable stream like this:
2022-09-01T19:57:49 Azure Event Log: Exchange Set-MailboxPlan: ExchangeAdmin, User_type: Microsoft_datacenter_operator, User_name: NT_AUTHORITY\SYSTEM_(Microsoft.Exchange.Servicehost), ClientIP: no_ip, ResultStatus: True, ObjectId: XA001.PROD.OUTLOOK.COM.., OriginatingServer: XA00..
Where we also translate the RecordIds, User_Type_Ids to their readable names.
Breakdown of Exchange Logs
As we mentioned before, the Exchange logs are broken into 3 main categories (or Record Types):
| ID | Event | Description |
|---|---|---|
| 1 | ExchangeAdmin | Events from the Exchange admin audit log. |
| 2 | ExchangeItem | Events from an Exchange mailbox audit log for actions that are performed on a single item, such as creating or receiving an email message. |
| 3 | ExchangeItemGroup | Events from an Exchange mailbox audit log for actions that can be performed on multiple items, such as moving or deleted one or more email messages. |
And each one of those categories can have many operations:
Update
SoftDelete
Create
MoveToDeletedItems
HardDelete
To match a specific action the user performs in their Exchange account.
For example, when a user deletes an email, it is a "SoftDelete" by default. Or when
someone sends an email, it is on the "Create" category. Translating that into a log, if someone is updating a calendar, it would be logged as:
2022-09-04T21:54:47 Azure Event Log: Exchange Update: ExchangeItem, User_type: Regular_user, User_name: dcid@test.com, ClientIP: 1.2.3.4, ResultStatus: Succeeded, LogonType: 0, ClientInfoString: Client=REST;Client=RESTSystem;;, Item_Path: \Calendar\Daniel C, OriginatingServer: CO123 (a.b.c.d), Item_Subject: Weekly Meeting
Allowing you to see that an Update was made to an ExchangeItem, in this case a Calendar item for Daniel, with the subject "Weekly Meeting".
Another example is when someone deletes an email, it also gets logged:
2022-09-01T21:58:22 Azure Event Log: Exchange SoftDelete: ExchangeItemGroup, User_type: Regular_user, User_name: dcid@test.com, ClientIP: 2.3.4.5, ResultStatus: Succeeded, LogonType: 0, ClientInfoString: Client=MSExchangeRPC, ClientProcessName: OUTLOOK.EXE, Item_Path: \Drafts, OriginatingServer: C123..., Item_Subject: RE: Reminder: Waiting for you to sign document
Where you can see it was done via Outlook.exe, from Drafts for an email with the subject "Waiting for you to sign a document".
For a large organization, those logs can be very busy, as any time someone creates an email, deletes an email, updates a calendar, replies, etc, it will get logged. It will also include their IP, and the subject of the email.
Inside Trunc you have the option to ignore those verbose Exchange emails and focus only on the admin and major level Exchange events by disabling the "Exchange Activity Log" via the Setup page. For other SIEM/Logging products, you can likely filter the ExchangeItem and ExchangeItemGroup events and focus on the ExchangeAdmin record type.
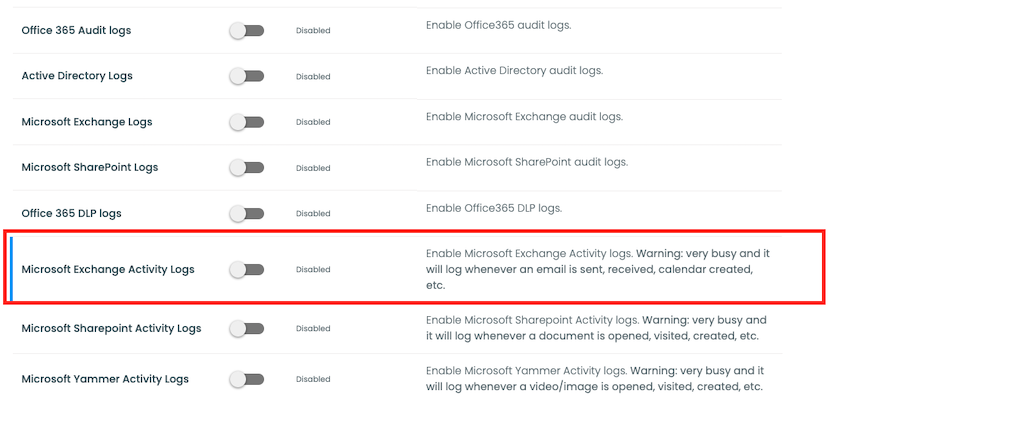
The ExchangeAdmin record type offers more categories, for things like:
Add-MailboxPermission
Remove-MailboxPermission
Set-Mailbox
Set-ConditionalAccessPolicy
These appear to be more interesting from a security perspective, allowing an admin to detect and archive whenever a change is made to a user.
If you use Office 365, we recommend setting up your logs and monitoring them closely.
Logging Guides
We love logs. In this section we will share some articles from our team to help you get better at logging.
Trunc Logging
Logging for fun and a good night of sleep.
- Real time search
- Google simple
- Cheap
- Just works
- PCI compliance
Latest Articles
Latest articles from our learning center.
- 2025-07-22Early Scans for CVE-2025-53771 (SharePoint Vulnerability) Detected
- 2025-06-03Investigating the 'slince_golden' WordPress Backdoor
- 2025-05-30Vulnerability Scanner Logs: WPScan
- 2025-05-29Web Scanning, Development Hygiene, and File Exposure Risks
- 2025-05-29Troubleshooting Remote Syslog with TCPDUMP
- 2025-05-29Logging basics: Syslog protocol in detail
Contact us!
Do you have an idea for an article that is not here? See something wrong? Contact us at support@noc.org
Tired of price gouging
- Clear pricing
- No need to guess
- Real people
- Real logging


 Get
Started
Get
Started