The Mozlila User Agent Bot
 Oct 13, 2022
Oct 13, 2022
If you have a website and spend any time analyzing your logs, you will likely find hacking attempts
coming with a user agent "Mozlila" (notice the typo?).
There are so many attacks using this user agent that many security tools and WAF (web firewalls) block it
automatically.
Also, if you search online, you will see many questions (and github issues) talking and asking about this user agent. The concerns stems from malicious activities it is performing.
Things like trying to find backup wp-config files:
185.220.101.134 - - [03/Jan/2021:11:54:29 +0000] "GET /wp-config.php.bkp HTTP/1.1" 404 488 "https://www.google.com/search" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36"
Or looking for backdoors:
137.220.48.110 - - [15/Jul/2022:06:53:00 +0000] "POST /ALFA_DATA/alfacgiapi/perl.alfa HTTP/1.1" 404 373 "www.google.com" "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36"
Or trying to exploit vulnerabilities:
2020-05-28 04:58:36 W3SVC1536 JASMINE 143.95.251.7 GET /wp-admin/admin-ajax.php action=revslider_show_image&img=../wp-config.php 80 - x.y.118.132 Mozlila/5.0+(Linux;+Android+7.0;+SM-G892A+Bulid/NRD90M;+wv)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Version/4.0+Chrome/60.0.3112.107+Moblie+Safari/537.36 - site 404 0 2 1405 556 296
Or trying to discover internal environment variables:
52.188.59.255 - [23-Oct-2020 23:40:36 Asia/Riyadh] "GET /admin/.env :443" 404 - Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36
The same user agent is always there. A typo of Mozilla (Mozlila), setting the system as Android 7.0 and using an old Chrome/60. Which makes us curious, where did this user agent come from?
Looking at our own logs, and public Github repositories, we see log entries starting in Feb/2020 using the same user agent. Our earliest recorded event was:
[27/Feb/2020:05:00:20 +0300] 500 212.227.164.114 site.com GET /.env HTTP/1.1 "Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36" "-" 33357
While curious, it did little to tell us where this user agent came from. Why would so many attacks be using it? Could it be tied to a new scanner? Is it from the same hacking group? tool?
Mozlila User Agent Attacks
Our best source of web data comes by way of our NOC.org WAF and CDN logs. We parsed the past 30 days to see what entries we could identify for that
user agent and found some 147,904 HTTP requests - almost all of them malicious:
Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36
The traffic has been consistent daily. You can see the breakdown via the Trunc dashboard here:
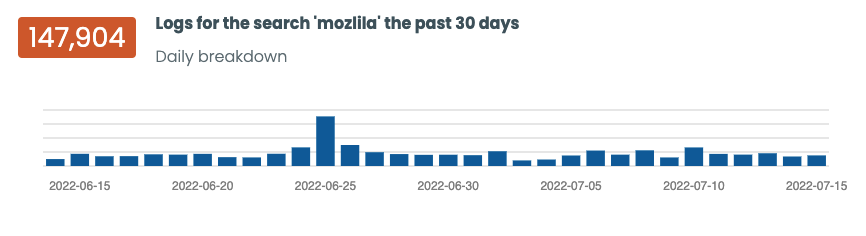
While consistent, we still had little insight in where it was coming from. So we turned to the IPs to see what they would share, if anything.
We found over 1,100 different IPs used this user agent to attack/scan our sites, with the top ones being:
Top IP Addresses
IP addresses with the most activity (out of 1,188).
Source IP Logs
36.78.87.254 10,023 (6.8%)
212.227.70.205 6,149 (4.2%)
20.248.243.32 4,883 (3.3%)
2.58.149.35 4,531 (3.1%)
217.160.48.108 4,153 (3.0%)
So 1,000 different IP addresses, with little connection between them. :(
We then moved on to better understand the types of attacks they were doing. Using the the Trunc terminal to parse the logs, here is a breakdown of the URLs being attacked.
> search mozlila | tail -n 90000 | cut -d " " -f 10 | sort -u
1789, /ALFA_DATA/alfacgiapi/perl.alfa
1756, /alfacgiapi/perl.alfa
1650, /wp-content/plugins/apikey/apikey.php?test=hello
1343, /plugins/content/apismtp/apismtp.php?test=hello
1265, /wp-plain.php
673, /wordpress/wp-class.php
670, /blog/wp-class.php
614, /wp-content/index.php
591, /wp-includes/wp-class.php
577, /wp/wp-includes/wp-class.php
572, /_profiler/phpinfo
531, /wp-content/plugins/dzs-zoomsounds/savepng.php?location=a57bze8931.php
531, /wp-content/plugins/ioptimizations/IOptimizes.php?hamlorszd
529, /wp-content/plugins/ioptimizations/a57bze8931.php
529, /wp-admin/admin-ajax.php?action=uploadFontIcon
528, /wp-content/plugins/dzs-zoomsounds/a57bze8931.php
528, /wp-content/plugins/arforms/js/filedrag/upload.php?fname=a57bze8931.txt
527, /wp-content/plugins/ioptimization/IOptimize.php?rchk
527, /wp-content/plugins/wp-engine-module/wp-engine.php
526, /wp-content/plugins/wp-engine-module/a57bze8931.php
525, /wp-content/uploads/kaswara/fonts_icon/a57bze8931/a57bze8931.php
523, /wp-content/plugins/ioptimization/a57bze8931.php
476, /aws.yml
370, /Backup
370, /.env.bak
305, /wp-content/plugins/dzs-zoomsounds/a57bze8931.php
304, //wp-content/themes/zakra/image.php
299, /xleet.php
This is interesting because it tells us that they are specifically targeting WordPress platforms, vulnerabilities and backdoors alike. So maybe it is a WordPress specific tool?
Where is the Mozlila User Agent Coming From?
Again, interesting data, but it still did not explain where the Mozlila comes from. Why are so many bots and scanners using it?
A bit more sleuthing and we noticed something interesting. Across multiple online repos we found multiple Python tools using the following script to connect to websites:
headers = {'Connection': 'keep-alive',
'Cache-Control': 'max-age=0',
'User-Agent': 'Mozlila/5.0 (Linux; Android 7.0; SM-G892A Bulid/NRD90M; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/60.0.3112.107 Moblie Safari/537.36',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'en-US,en;q=0.9,fr;q=0.8',
'referer': 'www.google.com'}
Could it be that simple? Couple it be nothing more than a classic case of copy / paste gone wrong?
Some of tools we found use this snippet to get a list of IPs or reverse IPs, or start a scan. Another example from "Rootinabox" Website grabber:
And many others, like this "WordPress finder" or this exploit.
So yes, we fear that it's nothing more than our beloved copy / paste doing a number on us all. Some poor soul introduced a typo that has been replicated across multiple tools / scanners
and the end result is having introduced a new user agent into the ecosystem. The silver lining seems to be is it is pretty safe to proactively block the user agent as it's mostly being used for malicious purposes.
Our recommendation? Watch for "MozLila" in your logs as it likely indicates scanning and malicious activity. Block if you can.
Logging Guides
We love logs. In this section we will share some articles from our team to help you get better at logging.
Trunc Logging
Logging for fun and a good night of sleep.
- Real time search
- Google simple
- Cheap
- Just works
- PCI compliance
Latest Articles
Latest articles from our learning center.
- 2025-07-22Early Scans for CVE-2025-53771 (SharePoint Vulnerability) Detected
- 2025-06-03Investigating the 'slince_golden' WordPress Backdoor
- 2025-05-30Vulnerability Scanner Logs: WPScan
- 2025-05-29Web Scanning, Development Hygiene, and File Exposure Risks
- 2025-05-29Troubleshooting Remote Syslog with TCPDUMP
- 2025-05-29Logging basics: Syslog protocol in detail
Contact us!
Do you have an idea for an article that is not here? See something wrong? Contact us at support@noc.org
Tired of price gouging
- Clear pricing
- No need to guess
- Real people
- Real logging


 Get
Started
Get
Started